CASE STUDY
We received a report from a client who fell victim to an online scam involving the domain parentafinancialservicesltd.com. Our mission was clear: conduct a thorough analysis of the domain, identify the threats, and help recover the lost funds.
Our investigation began with a detailed technical analysis of the domain parentafinancialservicesltd.com. Preliminary results revealed that the domain was created recently, on July 21, 2023, and was set to expire a year later. The domain was linked to an address in Finsbury, London, and its servers were located in Sofia, Bulgaria. These initial findings already raised our suspicions.
During the technical analysis, we discovered several key aspects:
- Cloudflare DNS Servers: The use of these servers suggested an attempt to hide the true location of the servers.
- Lack of AAAA and MX Records: This indicated that the domain was not intended for standard email use, which is unusual for legitimate financial firms.
- HTTP Redirection to an IP Address: The redirection could be an attempt to conceal the actual content of the site.
The next steps in the investigation involved gathering data from various security sources:
- Kaspersky: Identified the domain as a phishing site.
- MalwareURL: Marked the domain as phishing, indicating an attempt to steal personal data.
- SecLookup: Classified the domain as malicious, meaning it could contain harmful software.
- AlphaMountain.ai: Marked the domain as suspicious, suggesting potential threats.
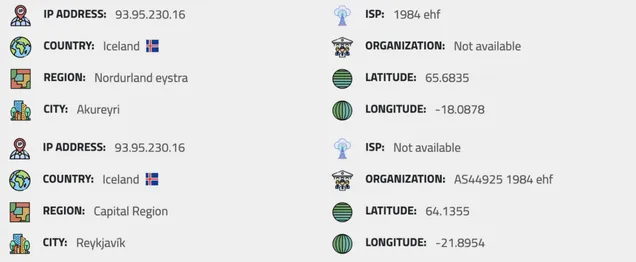
The IP address 93.95.230.16, associated with the domain, led us to Iceland. Contacting the abuse department at 1984 ehf in Reykjavik and further analysis revealed that this address was suspected of being used as a proxy/VPN, which could indicate attempts to hide the actual user's location.
We also discovered serious vulnerabilities in the Apache server, which could allow attackers to gain full control over the server or conduct Denial of Service (DoS) attacks.